For people in IT security who want to perform penetration testing on wireless networks, it is important to have a network adapter (NIC) which supports monitor mode and packet injection. A normal consumer NIC that you have in your laptop will most likely not support any of these features. Therefore, you would want to invest in an additional USB NIC.
A popular choice for penetration testing is a model called Alfa AWUS036ACH, because it supports a broad set of features needed for pentesting. At the same time it is rather inexpensive, so the bar to “just try it out” is low.
Kali Linux as most popular Linux distribution to perform such pentests does not support the Alfa AWUS036ACH out of the box. Especially when running Kali in a virtual machine you will have to keep in mind some additional details.
There are many questions online where people ask how to fix this issue. Many times answers are not provided or they are unnecessarily complicated. I used the following few steps for different setups and it always worked, so I hope this description will also be helpful for you.
When you connect the card to your computer and run iwconfig on call, you will not see your NIC:
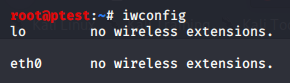
Kali does provide the necessary driver in its repositories, but you will probably first have to download it.
- Make sure that your USB NIC is connected with your computer
- In your Kali Linux, type the commands to download the driver as suggested by the Kali website:
apt-get update
apt install realtek-rtl88xxau-dkms- If you are running Kali in a virtual machine, you will also need to allow the virtual machine to connect to the USB device. You can do this in the running machine, but in my tests, this did not work directly after having installed the driver. I therefore recommend to shut down your VM and set the permission to access the USB NIC in the permanent settings for the VM. In VirtualBox you therefor have to right click on your VM and add the NIC to your VM.
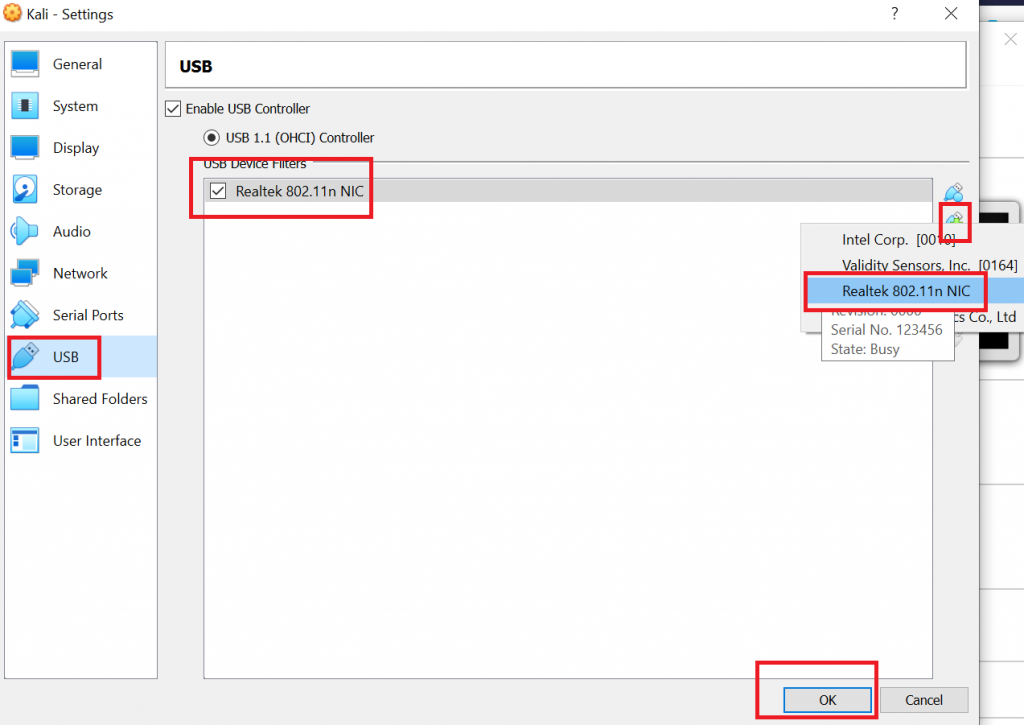
In case your Windows host system did not properly recognize the wireless adapter either, you can download and install drivers from the manufacturer’s website. You would then have to restart your computer and afterwards perform step 3 as described above.
- In some tests just adding the interface via VirtualBox settings did still not suffice, but I had to restart VirtualBox completely. Since this is done quickly, I recommend to do so just in case.
- Now, open VirtualBox and start up your Kali VM. When you now run iwconfig, the new USB NIC will be properly shown:
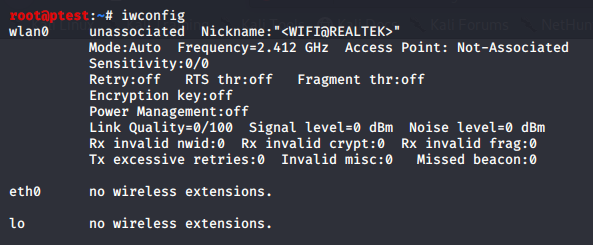
- As you can see in the screenshot above, your adapter will be in “Auto” mode. So, before you start your penetration tests, you will still have to bring it to Monitor mode. This can be done easily using airmon-ng:
airmon-ng start wlan0When you execute iwconfig once more, you will see that the adapter is now in Monitor mode.
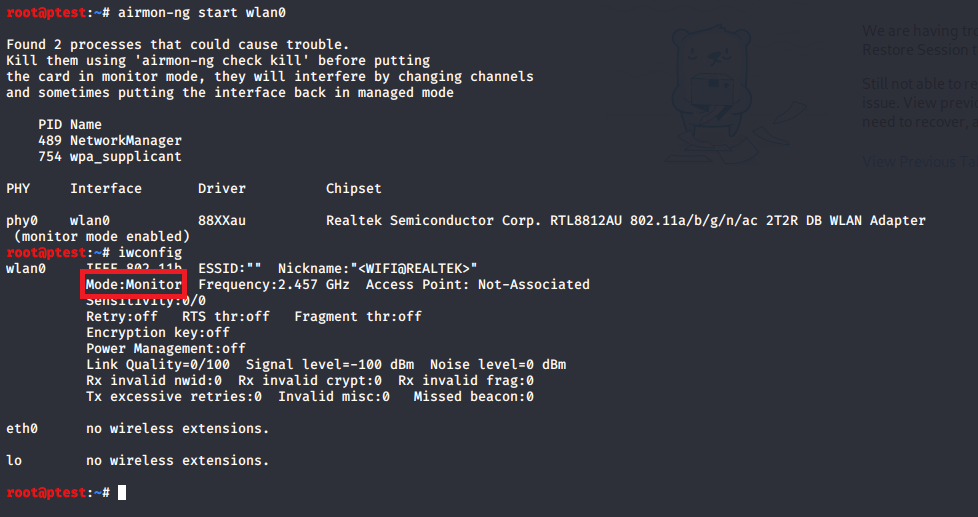
- One last preparatory step before you can start with your penetration tests is to stop processes which might otherwise return your NIC into another mode than Monitor mode. As airmon-ng already indicated above, you can accomplish this using the following command:
airmon-ng check kill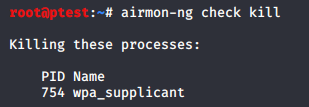
Although airmon-ng had shown a warning message about “Network Manager” being a possibly problematic process that should be stopped, it does not seem to touch it. At least the process is not listed under “killing these processes”. However, if you look at the upper right corner of your Linux, you should see that the network manager symbol was replaced by something that is labelled as “networking disabled”. So, although it does not say it, apparently the service was stopped, nonetheless. If you want to be 100% sure, you can try to stop the process using:
systemctl stop network-managerNow you are ready to perform your penetration tests using Alfa AWUS036ACH on your Kali Linux VM. The very useful aircrack-ng suite is already shipped along. Please keep in mind though that it is illegal to attack networks that you do not own or which you do not have permission to perform tests on.
Thank you for howto. How reliable has the adapter been so far? I’ve heard it’s not the most stable driver.
Hi Jonny,
Thank you for your comment. I agree with the observation that it is not the most stable utility I was working with. Both with the vendor’s original driver on Windows, and on Kali Linux I had to restart the setup from time to time, since some features suddenly stopped working. Unfortunately I do not know how to avoid these glitches completely, but at the very least restarts are quickly performed in a VM…
Good luck with your own tests!
Best regards,
Fabian
Why interface wlan0 is not changed to wlan0mon when monitor mode is enabled?
Hi Erma,
Thanks for your question! To be honest I don’t know exactly which component is the decisive one when it comes to interface naming. I understand that it either depends on the Kali version, or on the employed chipset:
“I know guides say it will change to “mon0″ but its either a distro or chipset variable. Mine changes to wlan0mon and it works as mon0 would.” -> https://www.reddit.com/r/HowToHack/comments/3klu9q/airmonng_displays_wlan0mon_instead_of_mon0/
“Both these methods place the wireless adapter into monitor mode except iwconfig keeps the monitor mode on wlan0 and airmon-ng starts monitor mode on mon0. ” -> https://forums.kali.org/showthread.php?28742-Difference-Between-quot-iwconfig-wlan0-mode-monitor-quot-and-quot-airmon-ng-start-wlan0-quot
I recently relocated to another country and the majority of my books where I could gain a better understanding are not here yet. However, for the functionality of the monitor mode, the naming of the interface has no influence. If you found out which component eventually decides on the interface naming, it would be great to know!
Sorry that I can not give you a more precise answer but I still hope it helped a bit…
Cheers,
Fabian
I followed these instructions and got to the point where the drivers are successfully installed. However, iwconfig still does not show wlan0. Does it matter that my Kali is 2020.4? Not sure what else to do.
I’m experiencing the exact same issue as you, have you been able to find a solution yet?
Hi David, Josh,
Sorry to hear that you have trouble setting up your NIC.
I checked my old VMs and extracted some further build information for you. The setup as described in the tutorial here worked for the following configuration:
lsb_release -a:
Release: 2020.1
hostnamectl:
Virtualization: oracle
Kernel: Linux 5.4.0-kali4-amd64
Architecture: x86-64
cat /proc/version:
gcc version 9.2.1 20200203 (Debian 9.2.1-28) #1 SMP Debian 5.4.19-1kali1 (2020-02-17)
If you really can’t get in running on newer versions, you could try this older build.
Also, if I find time at some point, I’ll try with more recent releases of Kali.
Would be great if you could post it here in case you succeed.
Cheers,
Fabian
A full dist-upgrade is needed after installing the driver, then just reboot.
This one worked for me
https://gitlab.com/kalilinux/packages/realtek-rtl88xxau-dkms
Thank you so much a great guide to install this wonderful NIC.
Hey, I have done the first steps in the howto. But my adapter is still not showing when I type iwconfig. It still seems like virtualbox is not recognizing my adapter(awus036ach).
Thanks!
Hi, does this give you the ability to sniff 5Ghz WiFi traffic?
Hi,
According to the NIC’s hardware specifications this will work, yes.
Good luck and let me know about your experiences.
Cheers,
Fabian